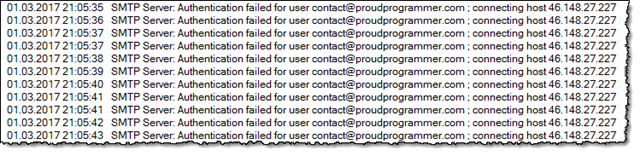
Finally I managed to stop the SMTP hacking, generating tons of "SMTP Server: Authentication failed for user ..."-messages
Have you ever seen a bunch of these in your Domino log-database?
If so, you are the victim of attempted SMTP Hacking. It means that someone is trying to log on to your server via the SMTP protocol. SMTP was primarily constructed for functionality and not so much security ![]()
Unnecessarily to say, it is a waste of cycles to have all this traffic hit your server, not to mention what could happen if they ever succeed entering the system! Obviously the perpetrators uses some sort of directory attack trying out both known and valid mail addresses, in addition to all sorts of other names.
Read on to see how I finally was able to stop specified IPs from even reaching the Domino server (hint, the Windows Firewall comes to rescue!)
Update March 7th, 2017: David Brown over at his site https://port1352.wordpress.com (love the port1352-name!) took the time to chime in and tipsed me about his blog-post Disable SMTP-AUTH To Stop Relay Hackers In Their Tracks . I had actually seen this post too, but I could not get my head around that it would could actually be better to turn off SMTP-authentication in order to have better security. I asked a question on his post, and he posted a thorough answer to why this might be a good idea here. Thanks David for taking your time to answer this question!
Domino has many counter-measures to fight spam, and the Domino configuration document contains sections from blacklists and so forth. I think I over the years have tried all sorts of Domino configuration tricks to make these attempts being blocked.
Below you see some of my attempts to block the IP address
SpamGeek software from Daniel Nashed
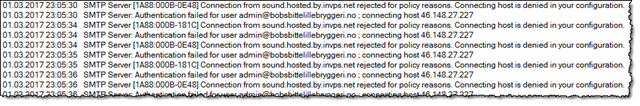
The best success up til date has been the fantastic tool SpamGeek from Daniel Nashed. It has the ability to at least refuse the furthe SMTP-connection from the IP address, so the log looks like this;
As you see, the SMTP hacking could still reach my server, but it was turned away due to policy reasons. Much better!
fail2ban
However, I want to block the perpetrating IP address to be completely blocked. The next attempt was to see what others have done.
If you try to search for “SMTP Server: Authentication failed for user” you find some good knowledge on the net, and one of the best is Protect your IBM Lotus Domino Server against brute force attacks on non HTTP ports by Christian Brandlehner . He shows how to get the fail2ban tool working with Domino. Probably one of the better, but it seems somewhat cumbersome to get going for me.
Let the WiFi-router block the IP address?
The next idea was to stop the incoming IP address from entering my network at all, let my WiFi router handle the firewall logic. Unfortunately it turned out that the IP-blocking feature on my router, was only for the outgoing traffic, like stopping a youngster in house from reaching non-approved web sites or services ![]()
Many others have asked the same question, and other router software such as Tomato seems to have such functionality. But then again, it felt cumbersome to reinstall the OS of my router in order to get an incoming IP address firewall.
Let the Windows Firewall do the job?
It turns out that the default Windows Firewall can block specified IP addresses!
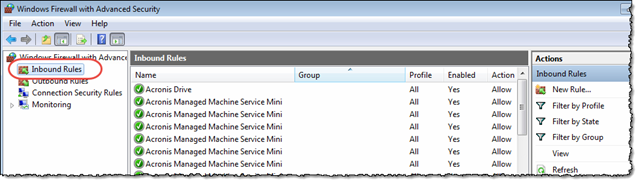
Launch the “Windows Firewall with Advanced Security”
Select the “Inbound Rules” tree in the navigator, like so:
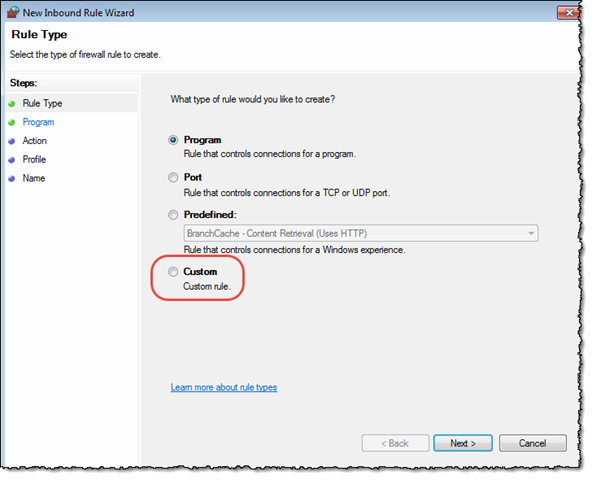
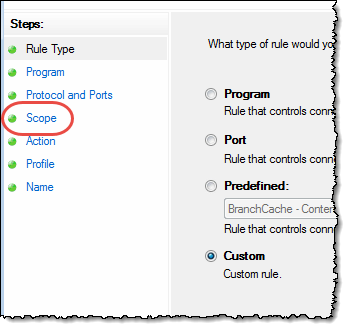
In the “Actions” area on the right, choose “New Rule …”. In the dialog box “New Inbound Rile Wizard”, choose “Custom”, like this:
As soon as you have selected “Custom”, Windows will add some more steps, like so;
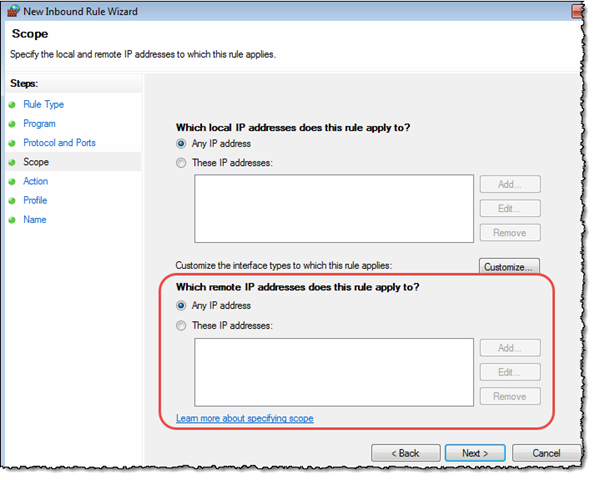
Choose the step “Scope”. Again Windows will instantly change the content in the dialog box, and you should see something like this;
The interesting part for us is the lower part, marked with a red rectangle above. The next part is to specify which IP addresses to block.
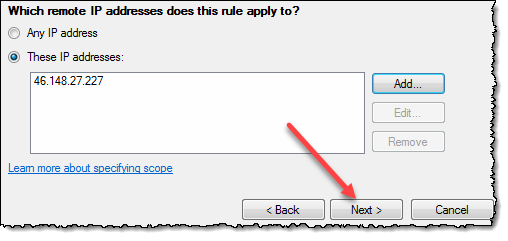
Choose the radio button “These IP addresses” to enable the Add, Edit and Remove buttons;
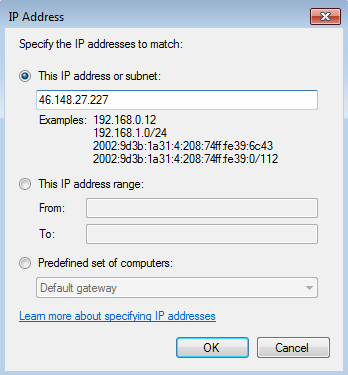
Click the “Add” button to add a new IP address (or a range if necessary!). Below the “IP address” dialog box is shown;
Click OK to return to the previous dialog box and see the IP address you have entered, like so;
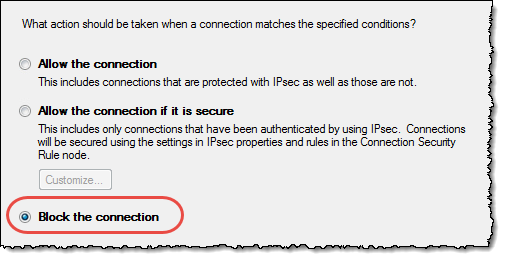
Repeat the add-process with all the IP addresses you want to block. When finished, click the “Next”-button. Then the wizard will ask you what you want to do with the IP-address(es) you have just specified;
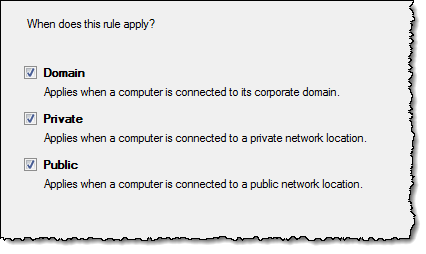
Now you choose “Block the connection”, click the “Next” button. The next question from the wizard is “When does this rule apply?” as seen below;
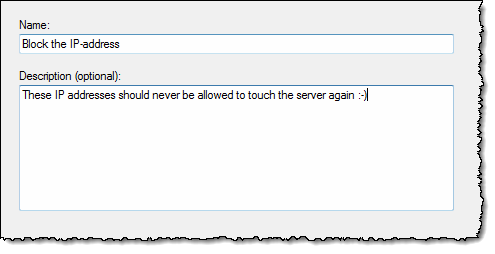
I just accepted all the default selections and click the “Next” button. The final step in the wizard is to give the new rule a name and a description;
When finished click the “Finish” button, and that was that for the specified IP-address(es) ![]()
Conclusion
The upside is that I could use standard and free Windows Firewall software to put some specified IP addresses to permanently rest.
And there lies the downside too. The Windows Firewall doesn’t have any logic to it, so you can’t for example tell it to “block IP address x.x.x.x after 10 repeated login attempts, for 60 minutes” or similar. This is more along the lines of tools like fail2ban or other firewall software. Another downside is that I can’t (at the present time at least) easily program or feed the list of blocked IP addresses. I could for example image something scanning my log-database for the sentence “SMTP Server: Authentication failed for user” and for every IP address, automatically feed it into the blocked IP address list. A quick search in my Windows Registry revealed that this might be programmable;
The Registry Key name is “HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\SharedAccess\Parameters\FirewallPolicy\FirewallRules”. Searching the net for the these keys reveal that somebody has been thinking along the same lines.
For my own part, I am happy to do my IP address blocking manually at the time being.
If you have experiences around these matters, recommendations or comments, please feel free to chip in!
Comments
If you don't need SMTP Auth enabled, here is an idea that I posted on my blog that might help quiet this issue for you: { Link }
Posted by David Brown At 22:25:04 On 03.03.2017 | - Website - |
Posted by Robert Ibsen Voith At 13:05:24 On 04.03.2017 | - Website - |
Posted by Lars Berntrop-Bos At 23:30:58 On 04.03.2017 | - Website - |
Thank you for sharing this, I've been struggling with this issue for quite a while. Made the simple change to my SMTP Site Document, restarted both the router and the SMTP task and no more annoying messages in my log. Thank you!
Posted by Gregg Eldred At 23:49:01 On 07.03.2017 | - Website - |
Posted by Angele Prefontaine At 14:54:03 On 23.02.2018 | - Website - |
Your post has certainly led me down the right path. I have multiple mobile phone users and thus cant turn off SMTP authentication.
The solution was a two fold approach:
1. Wrote a LotusScript agent that runs daily and parses thru all log.nsf documents created in the last 24 hrs, extracts the offending IPs and sends me an email at 9 AM everyday. I can share the script if people are interested.
2. Used a windows batch file that creates a windows firewall "incoming" rule that picks the IP list populated daily from step 1 above. I have a threshold of 200 IPs per firewall rule after which it creates a new one. Thanks to an internet poster Chris here in his help creating the batch file:
{ Link }
These two steps work very well and takes me 5 mins daily to update my firewall rules. Offending IPs are down to roughly 10 a day when typically I had over a 100.
I dont think the developers at HCL are remotely interested in plugging this loophole with their mail server, sadly.
Posted by Arvind Prasad At 15:00:47 On 19.03.2021 | - Website - |